GANs are part of the generative neural network models.
A genetic algorithm is an example of an “evolutionary calculation” algorithm, a family of AI algorithms inspired by biological evolution. These methods are considered as related to the meta-heuristic optimization area which means that they can be useful to find satisfying solutions for optimization problems (maximization or minimization), but do not provide guarantees of finding the optimal overall solution.
Solving a problem using the genetic algorithm requires representing its solution as a string of chromosomes (e.g. a matrix of bits) and also requires having a fitness function that can be used to evaluate solutions (!). A genetic algorithm works by maintaining a pool of candidate solutions (named generation). Iteratively, the generation evolves to produce the next generation that has candidate solutions with higher (better) fitness values than the previous generation. This process is repeated for a set number of generations or until a solution is found with the suitability value of the goal.
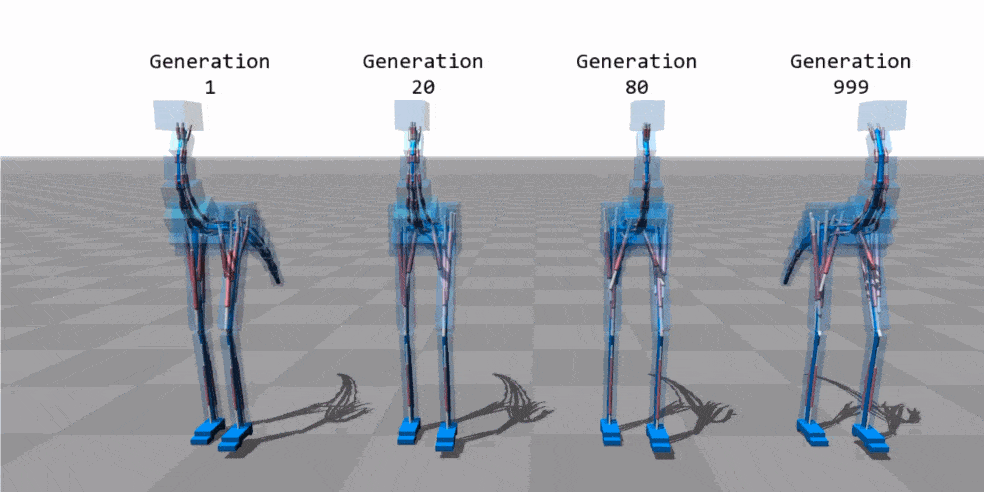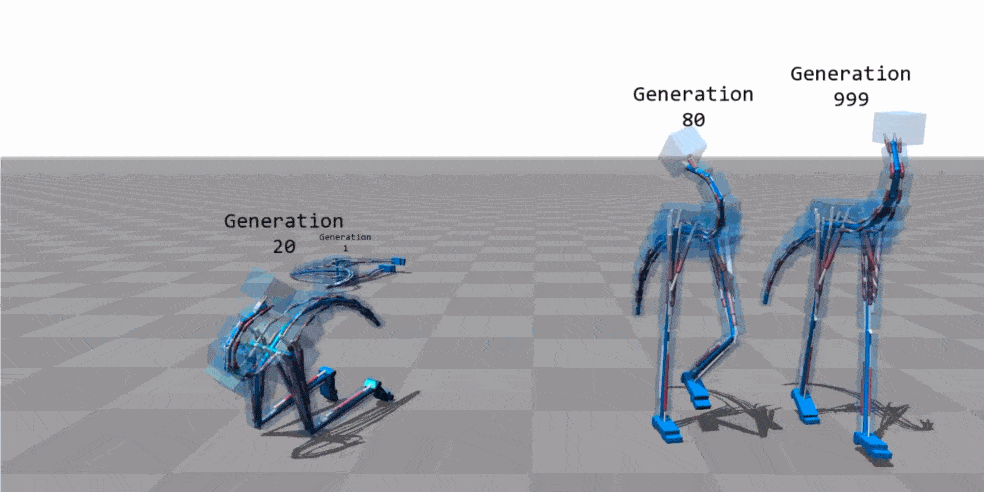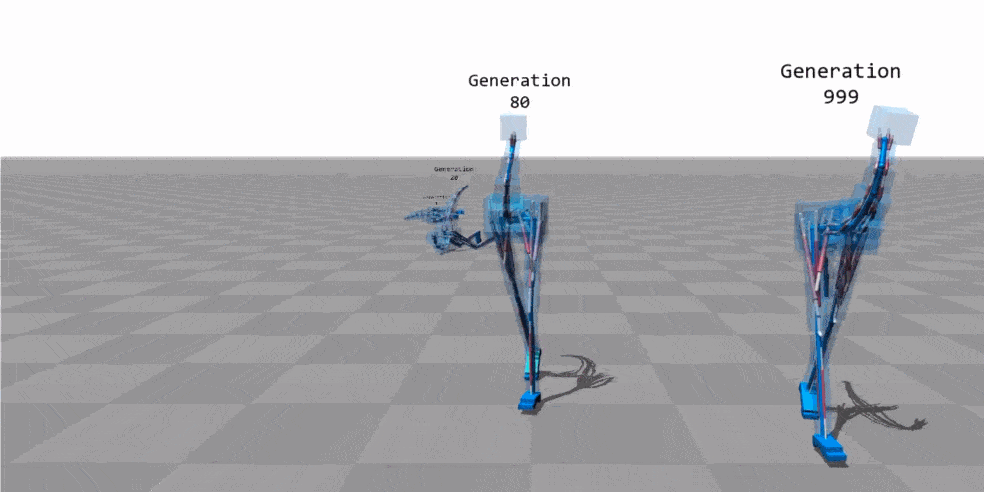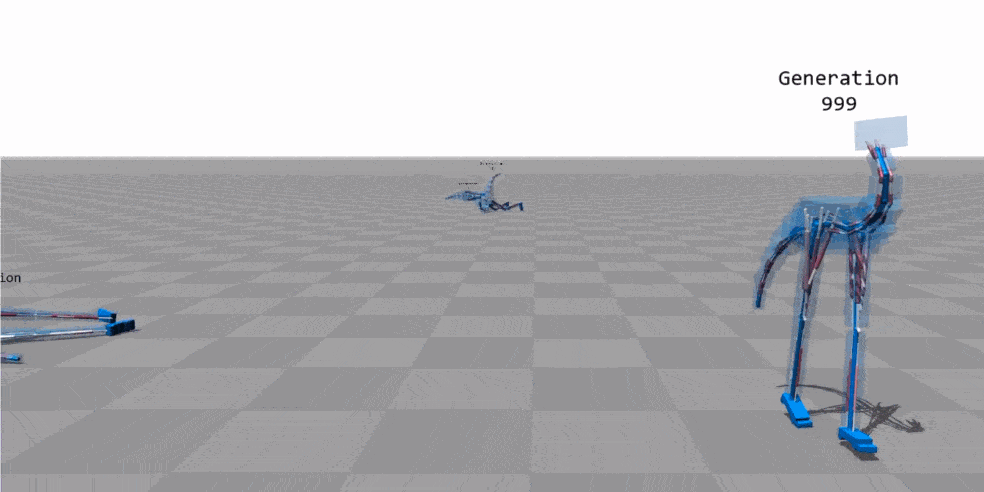
The image above shows a frame of an animation in which a genetic algorithm was used to learn the locomotion technique of a bipedal 3D model with a tail, no arms and a prominent neck (say “ostrich-morph”). In the image you can see how the different generations improve the posture of the model (in the animation you can also appreciate the almost “perfect” locomotion mode in the 999 generation).
The algorithm creates a new generation from the previous generation in a way inspired by biology that consists of 3 basic steps:
- Selection: The suitability of the members of the current generation is assessed, then the subset with the best fitness values is selected to act as parents for the next generation. In short, survival for the fittest.
- Crossover: Selected parent pairs are merged to generate a new child solution. Crossover can occur in different forms, the simplest form being the one-point crossover that divides the string representation of each solution into two parts in the same location, then concatenates the first part of a solution with the second part of the second to form the representation of the child solution.
- Mutation: In biology, mutation occurs with low probability when a child may have a characteristic that was not inherited from parents. Similarly, in the mutation phase of the genetic algorithm the solution of the offspring is perturbed with a very small probability.
The GAN Generative Adversarial Net(work)s, are a framework for the estimation of generative models through an adversary, or antagonist, process that involves the simultaneous training of a Generative model (Generator, or G) and a Discriminatory (Discriminator, D).
Adversarial Generative Networks (GAN) are architectures of Deep Neural Networks, composed of two networks, which oppose each other (hence the “contradictory”).
GANs were introduced in work by Ian Goodfellow and other researchers at the University of Montreal, including Yoshua Bengio, in 2014.
Referring to GANs, Facebook research director Yann LeCun called contradictory training “the most interesting idea of the last 10 years in ML.”
The potential of GANs is enormous because they can learn to mimic any distribution of data. That is, GANs can be instructed to create worlds impressively similar to ours in any domain: images, music, speech, prose. They are robot “artists” in a way, and their output is impressive.

Above “works of art” created by GAN algorithms.
To understand how GANs work, it would be useful to know how generative algorithms work, and for this reason, comparing them with discriminatory algorithms is useful.
Discriminating algorithms try to classify input data; meaning that, given the characteristics of a data instance, they predict a label or category to which that data belongs.
For example, given all the words in an e-mail message (the data instance), a discriminating algorithm might predict whether the message is spam or not spam.
Spam is one of the labels and the set of words collected from the email are the characteristics that make up the input data.
Then discriminating algorithms map the characteristics of the labels. They are explicitly interested in that correlation.
One way to guess how generative algorithms work is to think they do the opposite. Instead of predicting a label based on certain functions, they try to predict the characteristics provided by a particular label. The question a generative algorithm tries to answer is: “assuming this email is spam, how probable are these features?”
While discriminating models are concerned with the relationship between y and x, generative models are concerned with “how x is obtained”.
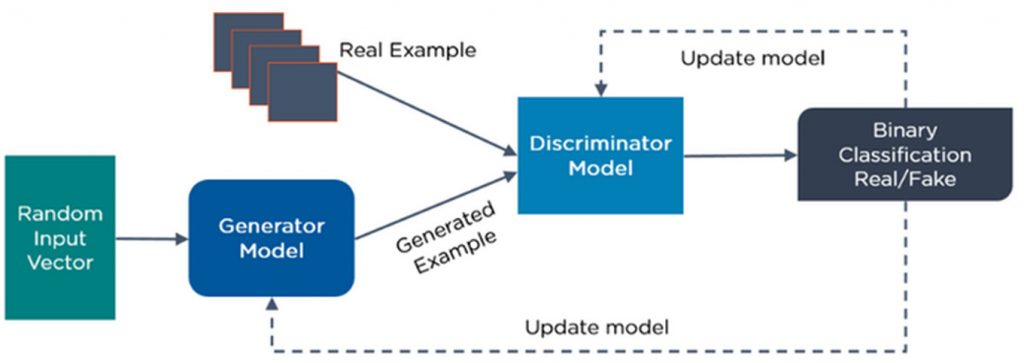
Another way to think about the functioning of GANs is to distinguish the discriminative from the generative in this way:
- Discriminatory models learn the boundary between classes.
- Generative models model the distribution of individual classes.
We can exemplify the logic of GAN and imagine it as the opposition of a counterfeiter and a policeman in a game of cops and thieves, where the counterfeiter is learning to pass false notes and the cop is learning to detect them. Both are dynamic; meaning that the policeman is also in training, and each side learns the methods of the other in a constant escalation.

Above is an example of a musical score generated through GAN algorithms.

Above is another example of using GAN through a technique for synthesizing human images by combining and overlaying existing images and videos on source images or videos.
An example that is causing a sensation in this period is the famous DeepNude algorithm based on GAN architecture.
https://github.com/stacklikemind/deepnude_official
Humanativa is experimenting with GAN neural networks to create a system for deriving patterns from compromised passwords.
This solution will have a dual purpose: on the one hand to improve the “password cracking” activities (recovery of passwords from data stored or transmitted by a computer system in encrypted form) performed by Penetration Testers (or “Ethical Hackers”) during verification activities, necessary to inform the Customer about the risks related to the passwords chosen by its users or employees. On the other hand, to offer companies a solution that can be integrated with authentication systems to assess the robustness of the passwords currently in use, verifying their distance and derivability from currently compromised passwords.

